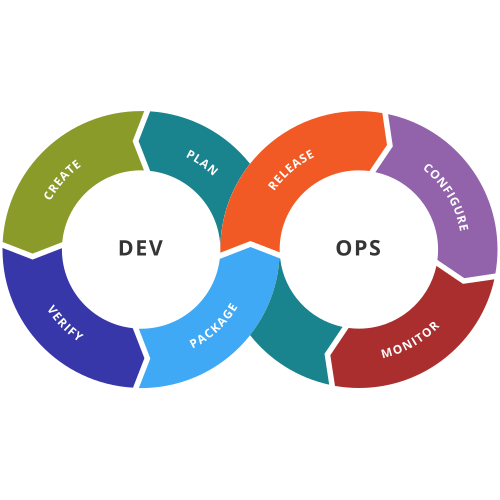
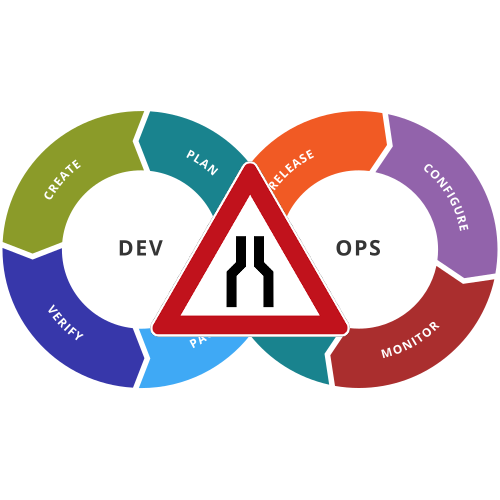
In the previous post I talked about bottlenecks in organizations, with a view from the DevOps transformation perspective. This article will focus on the close relation between the organizational structure and the culture.

Years ago, there was a worldwide tendency to adopt ITIL in the IT departments of all organizations, big or small. This, together with the wide adoption (although misunderstood by most) adoption of COBIT led to big and small companies setting up clear pillars, where the focus was on the activity being done, instead of the product or service delivered to the customer.
Since the update to Prometheus 2.0, the documentation still has to catch up. Because I’ve been debugging a custom written exporter, some unwanted metrics landed in my Prometheus. This is how to delete those series.

This guide will show you how to deploy Proxmox VE 5 with KVM Routing and NAT on a Hetzner server with focus on networking and DHCP/DHCPv6.
Ever since I’ve started hosting my own domains, I’ve searched for ways to automate the website provisioning. Normally, the documentation includes the information on configuring your infrastructure based on roles. But if you have a webserver role for all your minions it doesn’t help with the individual provisioning I am aiming at.


I’ve managed to move the blog away from tumblr.com to my own hosted server. I’m celebrating by deleting old (and obsolete) posts from my blog.
I’m curious to see how much success I’ll have in writing new articles.

Tired of always being afraid someone will hack into your Linux computer/server? One of the most important steps is to make sure the attacker can’t log in with the “root” account. In order to do this, you have to
Article target: web developers
How to bypass the Vodafone transparent proxy. For details about what it is, you can check out Vodafone transparent proxy - BMI Javascript at 1.2.3.4.



